| CPC H04L 9/0869 (2013.01) [G06F 21/12 (2013.01); G06F 21/52 (2013.01); G06F 21/54 (2013.01); G06F 21/64 (2013.01); H04L 9/0643 (2013.01); H04L 9/0877 (2013.01); H04L 9/0897 (2013.01)] | 18 Claims |
|
1. A method to enforce control flow integrity, the method comprising:
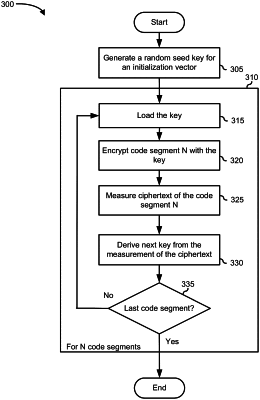
receiving a first encryption key, wherein the first encryption key is a randomly generated seed key;
retrieving a first one of a plurality of code segments ordered according to a sequence of execution;
encrypting the first code segment with the first encryption key;
measuring the first encrypted code segment resulting in a hash value;
applying a key derivation function to generate a second encryption key based on the hash value;
retrieving a second one of the code segments, wherein the second code segment is a next code segment in the sequence of execution; and
encrypting the second code segment with the second encryption key.
|