| CPC H04L 63/1425 (2013.01) [G06N 20/00 (2019.01); H04L 63/1416 (2013.01); H04L 63/1433 (2013.01); H04L 63/20 (2013.01); H04L 2463/121 (2013.01)] | 20 Claims |
|
1. A method comprising:
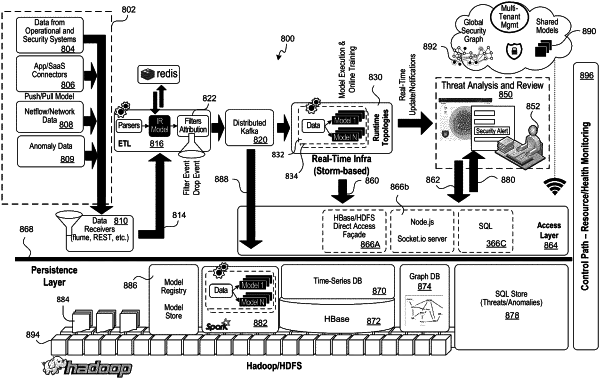
receiving, at a threat indicator detection system, first event data indicative of a first activity on a computer network and second event data indicative of a second activity on the computer network;
applying a first machine learning anomaly detection model to the first event data, by a real-time analysis engine operated by the threat indicator detection system in real time, to detect first anomaly data;
applying a second machine learning anomaly detection model to the first anomaly data and the second event data, by a batch analysis engine operated by the threat indicator detection system in a batch mode, to detect second anomaly data;
detecting third anomaly data using an anomaly detection rule; and
processing, by the threat indicator detection system using a threat indicator model, the first anomaly data, the second anomaly data, and the third anomaly data to identify a threat indicator associated with a potential security threat to the computer network.
|