| CPC H04L 63/1425 (2013.01) [H04L 63/20 (2013.01)] | 17 Claims |
|
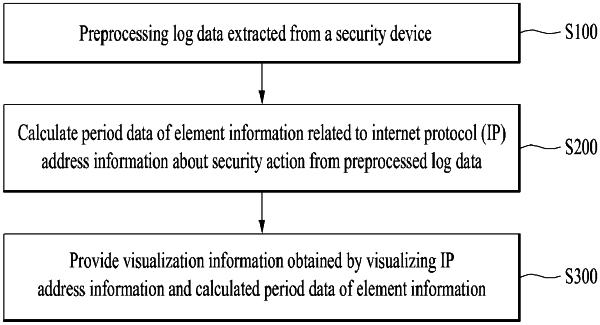
1. A method for visualizing security information, comprising:
preprocessing log data extracted from a security device;
calculating period data of element information related to IP address information about a security action based on the preprocessed log data; and
providing visualization information obtained by visualizing the IP address information and the calculated period data of the element information,
wherein the visualization information lists IP address information objects in a row or line in a tower shape based on a degree of security danger which is determined by an evaluation of danger in the IP address information,
wherein the method further comprises receiving a user input for selecting one of the IP address information objects,
wherein, in response to the user input, the visualization information further displays a log ring object in a cylindrical shape around the selected IP address information object, a circumferential direction of the log ring object representing a set time information and a vertical direction of the log ring object representing a corresponding amount of the log data, and
wherein the visualization information indicates a suspected attack on an IP address based on a degree of change in amount of the log data.
|