| CPC G06F 21/577 (2013.01) [G06F 21/566 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A system comprising:
one or more hardware computing system processors; and
memory storing a plurality of security engines and instructions that, when executed by the one or more hardware computing system processors, causes the system to:
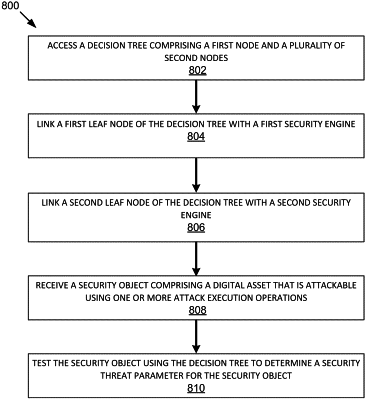
access a decision tree comprising a first node and a plurality of second nodes, wherein the plurality of second nodes comprise a first leaf node and a second leaf node; link the first leaf node comprised in the plurality of second nodes of the decision tree with a first security engine comprised in a plurality of security engines;
link the second leaf node comprised in the plurality of second nodes of the decision tree with a second security engine comprised in the plurality of security engines;
receive a security object comprising a digital asset that is attackable using one or more attack execution operations; and
test the security object using the decision tree to determine a security threat parameter for the security object,
wherein the security threat parameter is used to establish one or more remediation steps for mitigating against the one or more attack execution operations associated with the digital asset, and
wherein the testing the security object using the decision tree comprises:
determining, using the first security engine, a quantitative or a qualitative reputation parameter to assign to the security object, and
determining, using the second security engine, one or more threat attribute data associated with the security object, the threat attribute data comprising at least one of: a first threat attribute, a second threat attribute, a third threat attribute, or a fourth threat attribute.
|