| CPC G06F 21/556 (2013.01) [G06F 9/545 (2013.01); G06F 21/52 (2013.01); G06F 2221/033 (2013.01)] | 21 Claims |
|
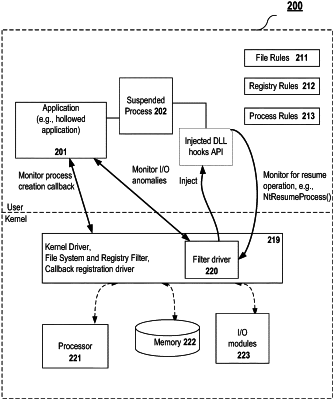
1. A method for preventing insertions of malicious processes, the method comprising:
monitoring, by a filter driver of a kernel mode of an operating system, active processes that are running in suspended mode; and
for each active process of the monitored active processes, by a filter driver of the kernel mode:
injecting a dynamic link library (DLL) into the active process to hook an application programming interface (API) of an application corresponding to the active process, wherein the DLL is injected for tracking commands for suspension and resumption of the active process;
monitoring file inputs and outputs of the application for anomalies while the active process is in the suspended mode;
when a command for resuming the active process is detected using the DLL, determining, based on the monitoring, whether a malicious process is inserted into the active process; and
allowing the suspended process to resume execution in response to determining that no malicious process is inserted in the active process.
|