| CPC G06F 21/577 (2013.01) [G06F 8/61 (2013.01); G06F 9/45558 (2013.01); G06F 21/31 (2013.01); G06F 21/554 (2013.01); G06F 21/87 (2013.01); G06F 2009/45562 (2013.01)] | 6 Claims |
|
1. A computer implemented method comprising:
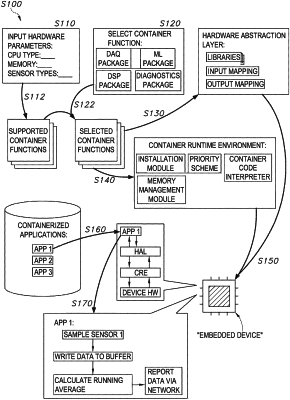
by a computer system, receiving a user input from a user associated with an embedded device comprising physical memory storing a native real-time operating system, the user input comprising a security technology configured to secure the embedded device;
by the computer system, accessing a set of hardware parameters characterizing the embedded device;
by the computer system, identifying a set of supported container functions based on the set of hardware parameters;
by the computer system, identifying a set of selected container functions based on the set of supported container functions, the set of selected container functions comprising the security technology;
by the computer system, generating a hardware abstraction layer for the embedded device;
by the computer system, generating a container runtime environment configured to execute, at the embedded device, a containerized application via the hardware abstraction layer, the containerized application comprising the set of selected container functions;
by the computer system, installing the hardware abstraction layer and the container runtime environment onto the native real-time operating system of the embedded device by:
allocating, by the native real-time operating system, a portion of the physical memory as a protected memory region from the containerized application; and
storing the container runtime environment and the hardware abstraction layer in the protected memory region; and
by the computer system, installing the containerized application onto the embedded device via the container runtime environment.
|