| CPC H04L 63/1441 (2013.01) [H04L 63/083 (2013.01); H04L 63/126 (2013.01)] | 20 Claims |
|
1. A method comprising:
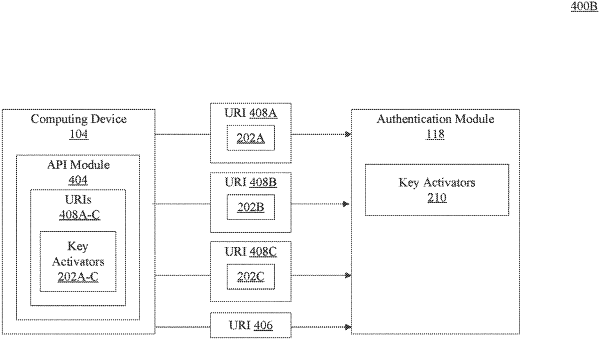
receiving key activators at an authentication module of a computing device, wherein the key activators include a first key activator and a second key activator incorporated into a sequence of Unified Resource Identifiers (URIs), wherein a first Unified Resource Identifier (URI) in the sequence of URIs includes the first key activator and a second URI in the sequence of URIs includes the second key activator;
extracting the first key activator from the first URI and the second key activator from the second URI;
validating, at the authentication module, the key activators, wherein the validated key activators are configured to activate the authentication module for authenticating a security credential during a predefined time interval;
subsequent to validating the key activators, receiving the security credential at the authentication module;
authenticating the security credential using the authentication module; and
transmitting an indicator indicating whether the authentication module authenticated the security credential.
|