| CPC H04L 41/0823 (2013.01) [H04L 9/0643 (2013.01); H04L 43/0888 (2013.01); H04L 45/745 (2013.01); H04L 47/24 (2013.01); H04L 47/32 (2013.01); H04L 47/36 (2013.01); H04L 61/5007 (2022.05); H04L 67/53 (2022.05); H04L 9/50 (2022.05)] | 20 Claims |
|
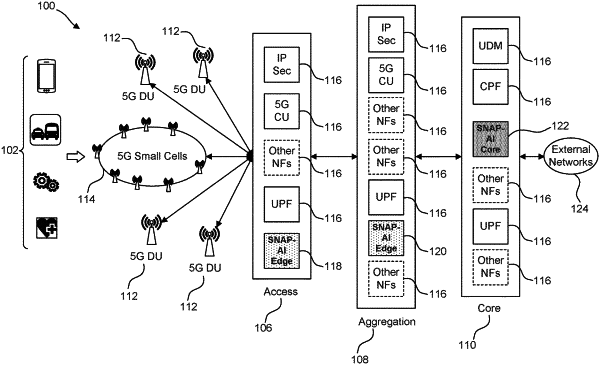
1. A method for providing traffic visibility in a network, comprising:
maintaining, by a computing device in communication with a network component, a rule table comprising a first rule with a first plurality of identifiers and a first action for generating a first characteristic relating to a flow of packets, wherein the computing device and the network component are located at an edge of the network;
receiving, by the computing device from the network component, during a first period of time, a copy of a first network packet with a second plurality of identifiers;
determining, by the computing device, that the second plurality of identifiers matches the first plurality of identifiers;
in response to the second plurality of identifiers matching the first plurality of identifiers, performing the first action of the first rule to generate the first characteristic associated with the first period of time, based on the copy of the first network packet;
receiving, by the computing device from the network component, a copy of a second network packet during the first period of time, and determining a predicted baseline of normalcy for a first network parameter during a second period of time based on the copy of the second network packet and the first characteristic associated with the first period of time; and
determining, by the computing device, that a second network parameter associated with the second period of time is an anomaly based on the predicted baseline of normalcy for the first network parameter, wherein the second network parameter is generated from a third packet received during the second period of time.
|