| CPC H04W 12/122 (2021.01) [H04W 12/106 (2021.01); H04W 12/73 (2021.01)] | 20 Claims |
|
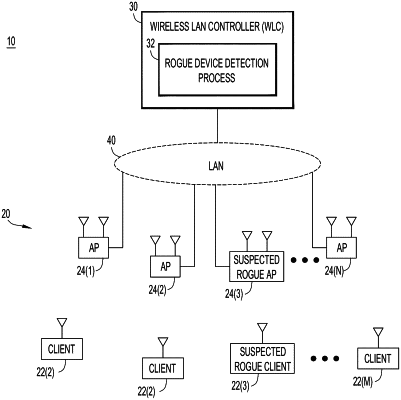
1. A method performed in a wireless network to detect a rogue wireless device, the method comprising:
detecting a suspect wireless device in the wireless network based on messages transmitted by the suspect wireless device using a first Media Access Control (MAC) address that is also used by a valid wireless device in the wireless network;
sending to the valid wireless device in the wireless network a request configured to cause the valid wireless device to change its MAC address, wherein the request is a wireless message sent using the first MAC address configured to cause the valid wireless device to change its MAC address to a new valid MAC address in order to reveal the suspect wireless device as a rogue device, wherein the new valid MAC address is selected from a valid un-attackable set of MAC addresses;
after the valid wireless device has changed its MAC address, observing messages transmitted by the suspect wireless device in the wireless network; and
determining that the suspect wireless device is a rogue device when the suspect wireless device continues to transmit messages using the first MAC address.
|