| CPC H04L 9/085 (2013.01) [H04L 9/0861 (2013.01); H04L 9/14 (2013.01); H04L 9/3073 (2013.01); H04L 9/3247 (2013.01); H04L 9/3268 (2013.01)] | 18 Claims |
|
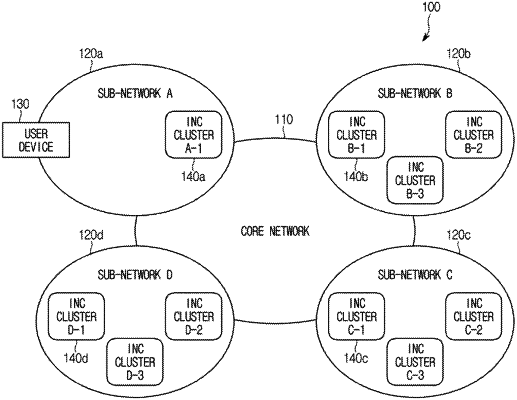
1. A method for protecting data for data name-based information centric in-network computing, the method comprising:
preparing, at a computing node, an encryption key pool that includes a security key for sharing a symmetric key used for encrypting result data according to a user's request and matching information;
preparing, at an INC agent receiving the user's request, a synchronization key pool for sharing the security key through the matching information;
creating, by the computing node, a processor for executing output processing of the result data and allocating a security key to the processor based on the matching information of the encryption key pool when a security key exists, the security key being allocated to the computing node which is determined to perform the request in the INC agent; and
removing, by the INC agent and the computing node, the allocated security key and the matching information from the synchronization key pool and the encryption key pool when the security key is allocated to the processor and creating a new security key and new matching information.
|