| CPC H04L 9/0822 (2013.01) [H04L 9/0825 (2013.01); H04L 9/3247 (2013.01)] | 14 Claims |
|
1. A method of performing multi factor authentication (MFA), the method comprising:
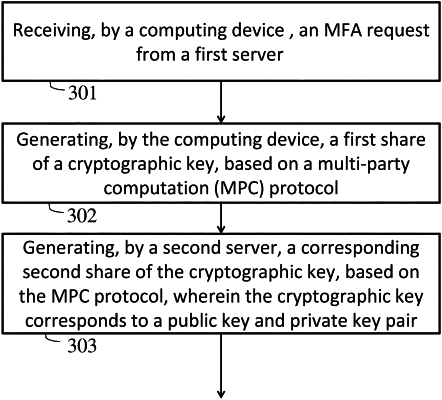
receiving, by a computing device, an MFA request from a first server;
generating, by the computing device, a first share of a cryptographic key, based on a multi-party computation (MPC) protocol;
generating, by a second server, a corresponding second share of the cryptographic key, based on the MPC protocol, wherein the cryptographic key corresponds to a public key and private key pair;
co-signing, by the computing device and the second server, the MFA request based on the MPC protocol, wherein the computing device signs the MFA request with the first share and the second server signs the MFA request with the second share;
verifying, by the first server, the signed MFA request;
encrypting, by the second server, the second share of the cryptographic key with a recovery public key;
sending, by the second server, the encrypted second share of the cryptographic key to the computing device;
detecting that the second server is unavailable;
retrieving, by the computing device, the recovery private key;
decrypting the encrypted second share of the cryptographic key by the computing device;
generating a group ID for a group of users of a shared MFA account;
receiving, by the second server, the group ID and the first share from the computing device;
distributing, by the second server, the first share among each of the users of the group;
enforcing a signing logic scheme for users of the group when signing with the shared MFA account; and
registering the computing device with the first server by sharing the public key with the first server.
|