| CPC H04L 9/0631 (2013.01) [H04L 63/0428 (2013.01)] | 11 Claims |
|
1. A method to encrypt an arbitrary binary data string (IFDS) of a first size in term of number of bits that is larger than a minimum size into an output file, and to decrypt said output file back into said IFDS, implemented in hardware using hardware blocks of specific functionality with said implementation integrated in a hardware system based application of broad functionality that requires said data encryption/decryption, and being assigned a unique implementation ID, comprising:
developing a set of unique, reference processing strings (PS) that is stored in a first partition of a first data storage device known as standard allocation memory (SAM) of a first number of storage locations with a first number of bits per each storage location, comprising:
each said PS is unique and has a number of bits of a unique sequence;
said set of PS is organized in a number of PS classes, with each said PS class comprising a number of said PS, with no two said PS classes having said PS of a same number of bits;
each of said unique sequence comprising one of the following:
a first unique sequence comprising of two or more consecutive groups of bits that alternate between 0 logic type and 1 logic type with each of said groups of bits being of a number of bits of one, two, or three bits of same said type and with a last said group in said unique sequence, called delimiter, being of four bits of same said type, in which by adding all said number of bits of all said groups in said unique sequence, a total number of bits that is smaller or equal to a first maximum number of bits is allowed;
a second unique sequence comprising of two or more groups of bits that alternate between 0 logic type and 1 logic type with each of said group of bits being of a number of bits of one, two, or three bits of same said type, wherein by adding all said number of bits of all said groups in said unique sequence, a total number of bits that is equal to said first maximum number minus one, or minus two, or minus three, is allowed;
a third unique sequence comprising a single group of bits of either 0 logic type or 1 logic type, with said single group being of a number of bits greater or equal to four;
developing one or more unique sets that are derived from said set of PS with each of said unique sets being stored in a partition of said SAM, comprising:
a set of primary root identifiers (RI) stored in a second said partition, wherein:
a number of unique said RI are developed for each said PS class, with each said RI having a number of bits of a unique sequence;
said set of RI is organized In a number of RI classes comprising a finite number of said RI with no two said RI classes having said RI of same number of bits;
a set of detail, stored in a third said partition, wherein:
each said detail has a number of bits;
each said detail follows a said unique RI such that said number of bits of said unique RI plus said number of bits of said detail equals said number of bits of a said unique PS;
said set of detail is organized in a number of detail classes comprising a finite number of said detail with no two said detail classes having said detail of same number of bits;
a set of pairs of said RI, known as a set of RI pairs, stored in a fourth said partition, wherein:
each said RI pair is unique and has a number of bits of a unique sequence;
each said unique RI pair is formed by pairing two unique said RI;
said set of RI pairs is organized in a number of RI pair classes comprising in a finite number of said RI pairs, with no two said RI pair classes having said RI pairs of same number of bits;
a set of root identifiers for said RI pairs, knows as a set of RI2, stored in a fifth said partition, wherein:
a number of unique said RI2 are developed for each said RI pair class, with each said RI2 having a number of bits of a unique sequences;
said set of RI2 is organized in a number of RI2 classes comprising a finite number of said RI2 with no two said RI2 classes having said RI2 of same number of bits;
a said unique RI pair is formed by a said unique RI2 followed by a group of number of bits called alternative, with said number of bits of said unique RI pair being equal to said number of bits of said unique RI2 plus said number of bits of said alternative;
with said RI, detail, RI pair, RI2, aggregately being called binary constructs, said RI classes, detail classes, RI pair classes, RI2 classes, aggregately being called classes, and said set of RI, set of detail, set of RI pair, set of RI2, aggregately being called sets;
aggregating said first, second, third, fourth, fifth partitions in a first storage bank of a second number of said storage locations, and developing one such storage bank that is part of said SAM for each value of a variable known as variable m, with said value being between one and a maximum value greater or equal to one, in which said first maximum number of bits of a PS in said first partition is assigned to be directly proportional to said value of said variable m;
interpreting an encryption/decryption key consisting of a total number of bits comprising a first number of bits to specify a said value of said variable m indicating a said bank used for encryption/decryption, a second number of bits to specify one or more of said sets within said bank that are modified for said encryption/decryption, a third number of bits to specify, within each of said sets specified by said second number of bits, one or more of said classes that are modified for said encryption/decryption, a fourth number of bits to specify within each of said class specified by said third number of bits, permutations that are performed among said binary constructs of said class to modify said class for encryption/decryption, with sa id interpreting being implemented using a first specialized functionality of a specialized controller (SC);
writing a second data storage device, known as operational memory (OM), in accordance to said interpreted encryption/decryption key, by employing a second specialized functionality of said specialized controller, comprising:
copying a said bank as specified by said first number of bits of said encryption/decryption key, from said SAM into said OM;
within said bank, modifying said one or more sets as specified by said second number of bits, with said modifying referring to modifying one or more said classes as specified by said third number of bits;
within each of said one or more sets, modifying said one or more of classes as specified by said third number of bits, with said modifying referring to performing permutations among said binary constructs of each said class as specified by said fourth number of bits;
within each of said one or more classes, modifying said class by performing said permutations among said binary constructs of said class as specified by said fourth number of bits, comprising reading said binary constructs and creating an order log of said storage locations of said binary constructs for said read, applying said permutations, and writing back said permutated binary constructs at same said storage locations as In said storage location order log, such that when same storage location of a specific said binary construct of a said class is read from said SAM called first read and from said OM called second read, a said first read to a said second read correspondence is the encryption of said specific binary construct, and a said second read to a said first read correspondence Is the decryption of said specific binary construct;
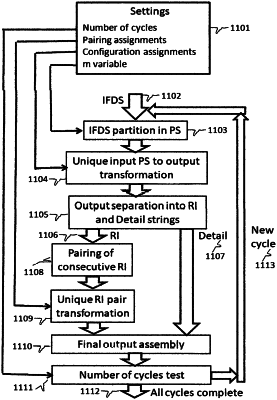
performing a group of operations to encrypt a said IFDS, producing one or more levels of encryption hierarchy, with said operations being implemented by said specialized controller through said specialized functionality, comprising:
partitioning said IFDS in a series of consecutive of said processing strings using said set of PS that are defined in accordance to said variable m for said OM bank, by accessing said first partition and recognizing a said PS in said IFDS, such creating said series of consecutive PS that occur in said IFDS, with every said consecutive PS receiving a first order number alternating as either odd or even with a first PS in said IFDS being odd, and such creating a first level of encryption hierarchy comprising in encrypting said PS in accordance to said specifying a said bank;
transforming every said consecutive PS immediately as it is said partitioned in accordance to said partitioning said IFDS step, said transforming being into corresponding said RI and said detail by accessing said second and third partition for each said consecutive PS, with said corresponding RI and detail receiving same first order number as said consecutive PS, with said transformation being in accordance to said first read to said second read correspondence of said second respectively third partitions, creating a second level of encryption hierarchy comprising in encrypting said RI and said detail that uses said first level of encryption hierarchy represented by said encrypted PS;
creating said RI pairs out of said encrypted RI of every two said odd and even consecutive PS in said IFDS immediately as they are said transformed in accordance to said transforming step, with said detail of said two RI in said RI pair creating a detail pair attached to said RI pair and with each detail preserving said first order number, and with said RI pair further accessing said fourth partition in accordance to said first read to said second read correspondence, creating a third level of encryption hierarchy consisting in encrypting said RI pairs that use said second level of encryption represented by said encrypted RI; and
assigning to every said RI pair, immediately as it is created by said creating said RI pairs step, a said RI2, by accessing said fifth partition, with said RI2 assignment being in accordance to said first read to said second read correspondence of said fifth partition, with said alternative of said RI2 being attached to said RI2, creating a fourth level of encryption hierarchy comprising in encrypting said RI2 that uses said third level of encryption represented by said encrypted RI pairs;
wherein said minimum size of said IFDS comprising said number of bits of two, said odd and even, consecutive PS;
generating an output file representing said encrypted IFDS, comprising:
writing in said output file, immediately as said RI2 is said assigned in accordance to said assigning to every said RI pair step, said RI2, said attached alternative, followed by said detail pair, for every said odd and even sequential PS for all said IFDS;
calling that an encryption cycle is completed once said output file is generated;
writing said implementation ID in said output file, and erasing said OM; and
performing a group of operations to decrypt a said output file, decrypting one or more levels of encryption hierarchy, with said group of operations being implemented by said specialized controller through said specialized functionality, the group of operations comprising:
decrypting said fourth level of encryption hierarchy, comprising:
locating in said output file a said RI2, by accessing said fifth partition in said OM;
decrypting said located RI2 in accordance to said second read to said first read correspondence of said fifth partition;
decrypting said third level of encryption hierarchy, comprising:
restoring an RI pair by accessing said fourth partition in said OM using said decrypted RI2 and said alternative attached to said RI2 during said assigning to every RI pair encryption step;
decrypting said restored RI pair in accordance to said second read of said first read correspondence of said fourth partition;
assigning an odd number to first RI in said decrypted RI pair and an even number to second RI in said decrypted RI pair;
decrypting said second level of encryption hierarchy, comprising:
matching said odd number RI in said decrypted RI pair to said odd number detail of said detail pair created during said creating said RI pair encryption step by accessing said second and third partitions of said OM, and similarly matching said even RI with said even detail;
decrypting said matched odd Ri-detail and said even RI-detail in accordance to said second read to said first read correspondence of said second and third partitions, with said decrypted RI and detail preserving said odd and even numbers;
decrypting said first level of encryption hierarchy and generating said decrypted IFDS, comprising:
restoring every said PS in said IFDS in accordance to said variable m represented by said OM bank by matching said odd respectively even decrypted Ri-detail with an odd respectively even PS by accessing said first partition;
generating said IFDS by writing in said IFDS every said restored odd respectively even PS in odd followed by even order, for all said output file;
calling that a decryption cycle is completed once said IFDS is generated,
and erasing said OM.
|