| CPC H04L 63/166 (2013.01) [H04L 5/0055 (2013.01); H04L 63/0485 (2013.01); H04L 69/166 (2013.01)] | 22 Claims |
|
1. At least one non-transitory computer-readable medium, comprising instructions that when performed by one or more processors, cause the one or more processors to:
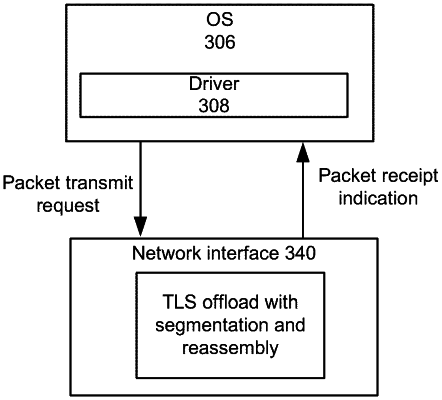
determine at least one offloaded capability of a network interface, the at least one offloaded capability comprising a first offloaded capability to perform a Transport Layer Security (TLS) cryptographic operation and segmentation operation on a first TLS record data prior to transmission and a second offloaded capability to identify a non-received packet with a portion of the first TLS record data and perform a re-transmission operation of a non-received packet with the portion of the first TLS record data and
enable the network interface to perform the second offloaded capability, wherein
to identify the non-received packet with the portion of the first TLS record data and perform the re-transmission operation of the non-received packet with the portion of the first TLS record data, the network interface is to determine the non-received packet with the portion of the first TLS record data and re-transmit solely the non-received packet with less than an entirety of the first TLS record data.
|