| CPC H04L 63/1483 (2013.01) [G06N 3/04 (2013.01); G06N 3/08 (2013.01)] | 12 Claims |
|
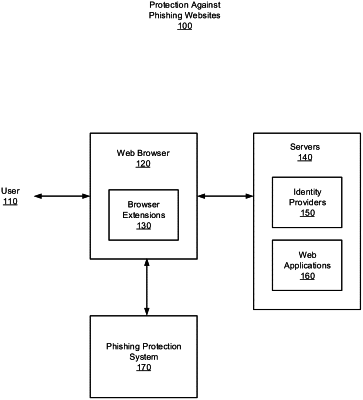
1. A computer system comprising:
a memory; and
at least one processor coupled to the memory and configured to:
train a neural network, the training including:
navigating to an identity provider (IdP) web page based on a domain name associated with the IdP web page;
capturing an image of the IdP web page;
generating variations of the image of the IdP web page by modifying attributes of the image of the IdP, the attributes including one or more of a background color, logos, fonts, dimensions, languages, words, or phrases; and
employing the variations to train the neural network;
capture an image of a browser web page;
identify a domain name associated with the browser web page;
employ the neural network to determine an image match where the captured image matches the image of the IdP web page; and
detect a phishing attempt in response to the determination of the image match, if the domain name associated with the browser web page differs from the domain name associated with the IdP web page.
|