| CPC H04L 63/1433 (2013.01) [G06F 40/30 (2020.01); H04L 63/102 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
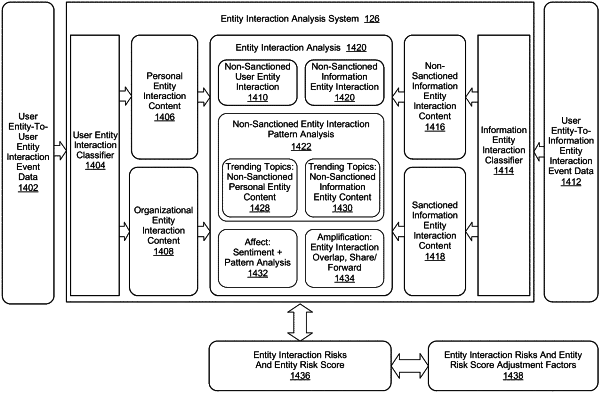
1. A computer-implementable method for performing an entity interaction risk analysis operation, comprising:
monitoring an entity, the monitoring observing an electronically-observable data source;
identifying an interaction between the entity and another entity based upon the monitoring, the entity being included within a first entity group;
analyzing the interaction between the entity and the another entity;
determining whether the interaction between the entity and the another entity is a non-sanctioned entity interaction, the non-sanctioned entity interaction comprising an interaction between the entity and the another entity whose enactment does not comply with a policy instituted by the first entity group; and,
performing a security operation via a security analytics system in response to the analyzing the interaction when the interaction is non-sanctioned, the security operation being performed by at least one of an endpoint device and the security analytics system, the endpoint device executing the security operation on a hardware processor associated with the endpoint device, the security analytics system executing the security operation on a hardware processor associated with the security analytics system.
|