| CPC H04L 63/1416 (2013.01) [H04L 61/5007 (2022.05); H04L 63/0272 (2013.01); H04L 63/029 (2013.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01); H04L 63/145 (2013.01); H04L 63/20 (2013.01); G06F 21/556 (2013.01)] | 20 Claims |
|
1. A computing system comprising:
one or more computer processors; and
one or more non-transitory computer-readable storage mediums storing program instructions configured for execution by the one or more computer processors to cause the computing system to:
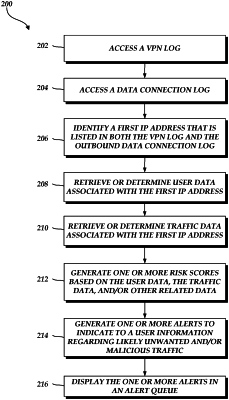
identify a first network address included in a first log and in a second log, wherein the first log identifies one or more second network addresses corresponding to one or more users granted access to a network, and wherein the second log identifies one or more third network addresses requested via the network;
determine based at least partly on the first network address, a score at least partly indicative of a likelihood that a malicious tunneling connection is present; and
initiate termination a first connection if the score satisfies a threshold value.
|