| CPC H04L 63/1416 (2013.01) [G06F 11/327 (2013.01); H04L 63/0263 (2013.01)] | 20 Claims |
|
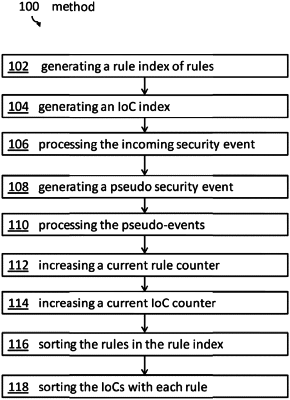
1. A method for processing security events by applying a rule-based alarm scheme for determining whether a received security event is considered as offense, the method comprising:
generating a respective indicator of compromise index for each rule in a rule index, each respective indicator of compromise index comprising indicator values of indicators of compromise to be used for a comparison against an attribute of a security event;
processing an incoming security event by sequentially applying the rules in the rule index, wherein processing the incoming security event comprises:
increasing a current rule counter relating to a triggered rule, wherein the triggered rule comprises a respective one of the rules that triggered an offense during the processing, and
increasing a current indicator of compromise counter pertaining to the triggered rule, wherein the current indicator of compromise counter comprises a different counter than the current rule counter;
sorting the rules in the rule index according to a rule likelihood of triggering an offense, wherein the sorting the rules is based on respective weighted rule counter values;
sorting, for each rule, the indicators of compromise in the respective indicator of compromise index according to an indicator of compromise likelihood of triggering an offense, wherein the sorting the indicators of compromise is based on weighted current indicator of compromise counter values; and
processing another incoming security event by sequentially applying the sorted rules contained in the rule index.
|