| CPC H04L 63/1416 (2013.01) [H04L 63/126 (2013.01); H04L 63/1466 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
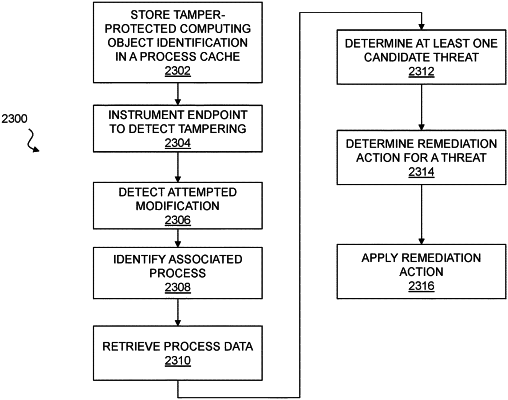
1. A computer program product comprising computer executable code embodied in a non-transitory computer-readable medium that, when executing on one or more computing devices, performs the steps of:
storing a cache in a kernel space of an endpoint of an enterprise network, the cache including one or more entries identifying one or more tamper-protected computing objects, each of the one or more entries in the cache cryptographically signed by an external trust authority;
instrumenting the endpoint to detect an attempted modification to one of the tamper-protected computing objects based on an interaction with the cache corresponding to the one of the tamper-protected computing objects; and
in response to detecting the attempted modification to the one of the tamper-protected computing objects:
determining a process associated with the attempted modification to the one of the tamper-protected computing objects;
determining that the process associated with the attempted modification is not one of the tamper-protected computing objects identified in an entry in the cache and cryptographically signed by the external trust authority;
determining a remediation action for mitigating at least one threat associated with the attempted modification; and
applying the remediation action to mitigate the at least one threat in the enterprise network, wherein the remediation action references the process associated with the attempted modification.
|