| CPC H04L 41/0893 (2013.01) [G06F 9/45558 (2013.01); H04L 12/4633 (2013.01); H04L 12/4641 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01)] | 21 Claims |
|
1. A method comprising:
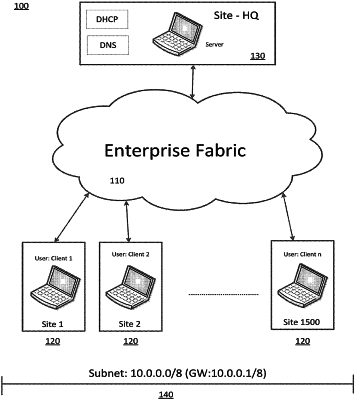
discovering that a plurality of endpoint hosts have joined an enterprise network, wherein the plurality of endpoint hosts comprise at least a first endpoint host and a second endpoint host;
wherein each of the first endpoint host and the second endpoint host are assigned a corresponding address within the enterprise network, and the first and second endpoint hosts are endpoints in the enterprise network;
after discovering the first endpoint host, assigning to the first endpoint host a first role from a plurality of roles within the enterprise network;
after discovering the second endpoint host, assigning to the second endpoint host a second role from the plurality of roles;
accessing a policy configuration defining allowable communications between endpoint hosts based on their respective roles,
wherein the allowable communications are defined as being only between hosts having different roles within the enterprise network;
generating instructions based on the policy; and
providing the instructions to one or more switches causing the one or more switches to permit or deny communication of data packets between the first and second endpoint hosts based on the first role and the second role.
|