| CPC G06Q 30/0185 (2013.01) | 17 Claims |
|
1. A pseudorandom batch code printing and product authentication system comprising:
one or more processors; and
a batch code printing application (app) comprising computing instructions configured to be executed by the one or more processors,
wherein the computing instructions of the batch code printing app, when executed by the one or more processors, are configured to cause the one or more processors to:
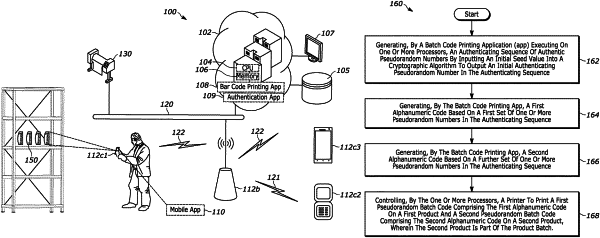
generate an authenticating sequence of authentic pseudorandom numbers by inputting an initial seed value into a cryptographic algorithm to output an initial authenticating pseudorandom number in the authenticating sequence,
wherein the initial seed value comprises a product date of a first product that is part of a product batch,
wherein each subsequent authenticating pseudorandom number in the authenticating sequence is generated directly or indirectly from the initial authenticating pseudorandom number whereby the initial authenticating pseudorandom number or a subsequent derivative thereof is input into the cryptographic algorithm to output a next authenticating pseudorandom number of the authenticating sequence,
generate a first alphanumeric code based on a first set of one or more pseudorandom numbers in the authenticating sequence,
generate a second alphanumeric code based on a further set of one or more pseudorandom numbers in the authenticating sequence, and
control, by the one or more processors, a printer to print a first pseudorandom batch code comprising the first alphanumeric code on the first product and a second pseudorandom batch code comprising the second alphanumeric code on a second product, wherein the second product is part of the product batch;
an authentication application (app) comprising instructions configured to be executed by the one or more processors,
wherein the computing instructions of the authentication app, when executed by the one or more processors, are configured to cause the one or more processors to:
determine an identified product date and a suspect alphanumeric code from a suspect batch code as printed on a suspect product,
generate a test sequence of test pseudorandom numbers by inputting the identified product date as a test seed value into the cryptographic algorithm to output an initial test pseudorandom number in the test sequence, wherein each subsequent test pseudorandom number in the test sequence is generated directly or indirectly from the initial test pseudorandom number whereby the initial test pseudorandom number or a subsequent derivative thereof is input into the cryptographic algorithm to output a next test pseudorandom alphanumeric number of the test sequence, and
generate an output comprising one of:
(1) an authenticating output indicating that the suspect product is authentic when the suspect alphanumeric code matches a test alphanumeric code derived from at least one test pseudorandom number of the test sequence; or
(2) a counterfeit output indicating that the suspect product is counterfeit when the suspect alphanumeric code fails to match a test alphanumeric code derived from at least one test pseudorandom number of the test sequence;
wherein generation of the output further comprises submitting one or both of the suspect batch code and the suspect alphanumeric code to an authentication database comprising a list of known counterfeit batch codes,
wherein the counterfeit output is provided in response when the one or both of the suspect batch code and the suspect alphanumeric code match at least one known counterfeit batch code identified within the known counterfeit batch codes, and
wherein the authenticating output is provided in response when the one or both of the suspect batch code and the suspect alphanumeric code fail to match at least one known counterfeit batch code within the known counterfeit batch codes.
|