| CPC G06F 3/0673 (2013.01) [G06F 3/061 (2013.01); G06F 11/3006 (2013.01); G06F 13/20 (2013.01); G06F 21/316 (2013.01); G06F 21/566 (2013.01); H04L 41/0663 (2013.01); H04L 63/1425 (2013.01); G06F 2213/40 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A method comprising:
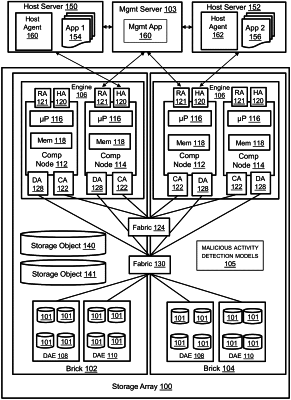
receiving, by a storage array from a plurality of host agents running on host servers, current host application awareness information comprising at least one host application role of a plurality of host application roles performed by instances of a host application;
observing, by the storage array, characteristics of input-output operations (IOs) by instances of the host application to access at least one storage object maintained for the host application by the storage array; and
using the current host application awareness information and the observed characteristics of IOs by instances of the host application to access the at least one storage object as inputs to a host application-specific model to predict that the at least one storage object is a target of malicious access activity.
|