| CPC G06F 21/577 (2013.01) [G06F 21/6218 (2013.01); G06F 21/552 (2013.01); G06F 21/565 (2013.01)] | 17 Claims |
|
1. A computer-implemented method, executed by one or more processors, comprising:
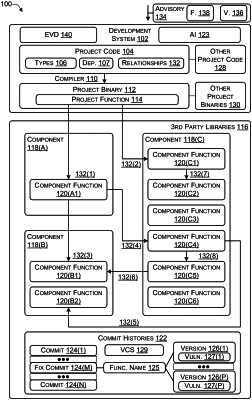
receiving a security advisory that include a description of a vulnerability;
accessing a version control system (VCS) used by a third-party library;
determining additional resources related to the vulnerability;
determining a set of code changes performed by project maintainers in the VCS;
identifying one or more fix commits that address the vulnerability;
identifying one or more functions with the vulnerability that have been changed by the one or more fix commits, wherein identification of the one or more functions with the vulnerability includes:
comparing one or more files corresponding to the one or more functions before and after a code change was made, and
identifying individual functions of the one or more functions that included the vulnerability and that have been modified to address the vulnerability;
performing a search for components and component versions that include the one or more functions with the vulnerability;
generating an enriched vulnerability description that includes identifiers of package versions that include:
fixed versions of the one or more functions; and
vulnerable version of the one or more functions; and
modifying project code in a development system to use the fixed versions of the one or more functions.
|