| CPC G06F 21/577 (2013.01) [G06Q 10/0875 (2013.01); G06F 2221/034 (2013.01); G06F 2221/2139 (2013.01)] | 25 Claims |
|
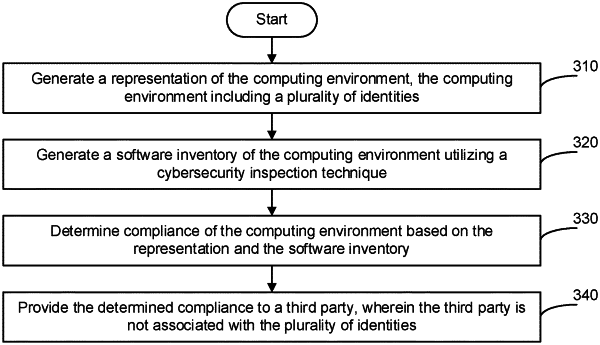
1. A method for providing third party compliance to computing environments without providing access thereto, comprising:
generating a representation of the computing environment, the computing environment including a plurality of identities;
generating a software inventory of the computing environment utilizing a cybersecurity inspection technique;
executing a database query on any one of the representation of the computing environment, the software inventory, and a combination thereof;
generating an alert in response to determining that the executed query returns a predetermined result;
determining compliance of the computing environment based on the representation, the software inventory, and the predetermined result; and
providing the determined compliance to a third party, wherein the third party is not associated with the plurality of identities.
|