| CPC G06F 21/568 (2013.01) [G06F 21/552 (2013.01); G06F 21/563 (2013.01)] | 19 Claims |
|
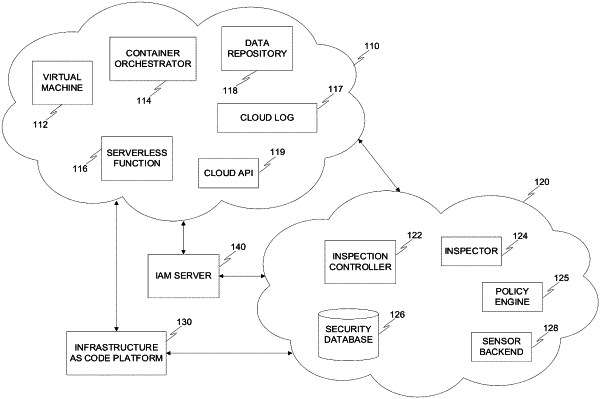
1. A method for identifying cloud identity misuse based on run-time time data and static analysis, comprising:
detecting a workload in a cloud computing environment;
configuring the workload to deploy thereon a sensor application, the sensor configured to detect data respective of a runtime process executed on the workload;
detecting an original disk associated with the workload;
generating an inspectable disk based on the original disk;
inspecting the inspectable disk for a cybersecurity object utilizing static analysis;
detecting in a log of the cloud computing environment an event based on an identifier of the workload, the log including a plurality of events;
inspecting a code object for an identity object, the code object utilized in deploying the workload in the cloud computing environment;
associating the runtime process with the event based on: an identifier of the workload, the identity object, and the cybersecurity object; and
generating an enriched log including an identifier of the runtime process associated with the event.
|