| CPC G06F 21/567 (2013.01) [G06F 21/562 (2013.01); G06N 3/04 (2013.01); G06N 3/045 (2023.01); G06N 3/08 (2013.01); G06N 3/084 (2013.01); H04L 63/1416 (2013.01); G06F 2221/032 (2013.01); G06N 5/01 (2023.01); G06N 7/01 (2023.01)] | 18 Claims |
|
1. An apparatus, comprising:
a memory; and
one or more processors operatively coupled to the memory, the one or more processors configured to:
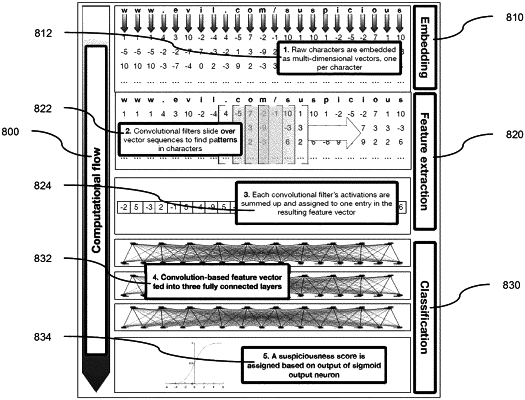
receive a string associated with an artifact;
convert each character in the string into a character vector to generate a set of character vectors;
apply a convolution matrix to the set of character vectors to define at least a portion of a feature vector;
provide the feature vector as an input to a machine learning model configured to receive the feature vector and generate as an output a classification indicating a maliciousness associated with the artifact based on the feature vector; and
detect the maliciousness associated with the artifact based on the output of the machine learning model.
|