| CPC G06F 21/554 (2013.01) [G11C 8/20 (2013.01); G11C 11/406 (2013.01); G11C 11/40603 (2013.01); G06F 2212/1052 (2013.01)] | 20 Claims |
|
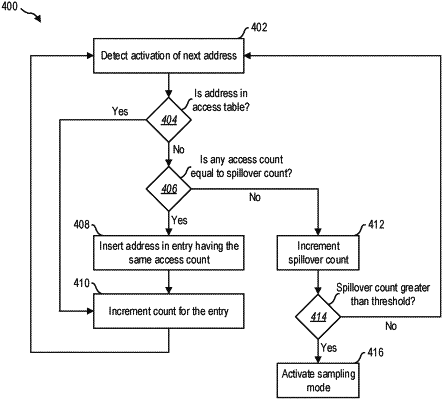
1. A method implemented by a memory controller for detecting and mitigating a row hammer attack on one or more memory rows of a dynamic random access memory (DRAM) device, comprising:
maintaining an access count table for a memory sub-bank, the access count table including memory row addresses within the memory sub-bank, a plurality of access counts indicating estimated activation counts for the memory row addresses, and a spillover count based on memory row accesses for at least one memory row address not included within the access count table;
detecting that the spillover count is greater than or equal to a threshold count, the threshold count being associated with a prediction of a possible aggressor row from the memory sub-bank;
based on detecting that the spillover count is greater than or equal to the threshold count, activating a sampling mode for the memory sub-bank by generating a random number and determining if the random number falls within a sampling threshold; and
reporting a memory row address as an aggressor address corresponding to the possible aggressor row based on whether the random number falls within the sampling threshold.
|