| CPC G06F 21/44 (2013.01) [G06F 21/565 (2013.01); G06F 21/445 (2013.01); G06F 21/554 (2013.01); G06F 21/561 (2013.01); G06F 21/566 (2013.01); H04L 63/029 (2013.01); H04L 63/101 (2013.01); H04L 63/20 (2013.01)] | 21 Claims |
|
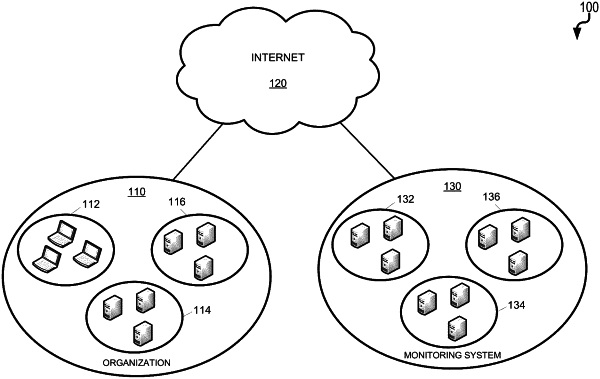
1. A method for implementation by one or more computing devices comprising:
inferring, in response to a trigger, a program identity of an unknown binary;
executing one or more authentication factors to authenticate the inferred program identity of the unknown binary as being one of a plurality of different programs, the one or more authentication factors comprising one or more executable integrity tests in which scripts forming part of the unknown binary are cryptographically verified as being from a known source;
determining that the unknown binary has been modified relative to a known binary;
determining whether modifications of the unknown binary are congruent modifications or divergent modifications, the congruent modifications comprising a modification to a data representation of the known binary which preserve a program nature of the unknown binary, the divergent modifications comprising a modification to a data representation of the known binary which change the program nature of the unknown binary;
selectively providing the unknown binary with access to system resources based on the program nature of the authenticated program identity and based on the determination of whether the modifications of the unknown binary are said congruent modifications or said divergent modifications.
|