| CPC G06F 21/44 (2013.01) [H04L 9/0866 (2013.01); H04L 9/16 (2013.01); H04L 9/3271 (2013.01); H04L 63/0428 (2013.01); H04L 63/08 (2013.01); H04L 63/0876 (2013.01)] | 20 Claims |
|
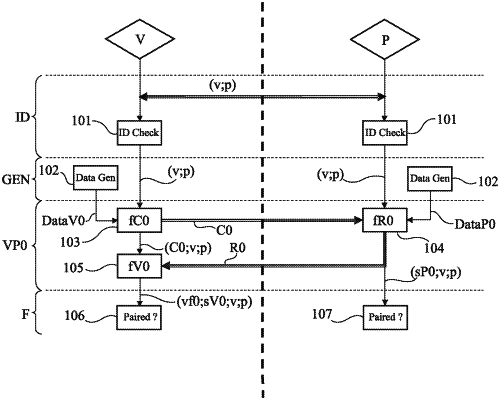
1. An authentication method of a prover device to a verifier device, the method comprising:
at least two successive verification operations, each operation comprising, successively:
generating, by the verifier device, first data from second data generated by the verifier device in a preceding verification operation;
sending, by the verifier device, the first data to the prover device;
generating, by the prover device, third data and fourth data used by a following verification operation, by applying a first function taking as input at least the first data and the fourth data generated in the preceding verification operation;
sending, by the prover device, the third data to the verifier device;
verifying, by the verifier device, the third data using a second function taking as input the first data and the third data; and
outputting, by the verifier device, information indicating whether the verification was successful, and the second data used by the following verification operation; and
authenticating the prover device to the verifier device in response to:
for each verification operation, the information indicating that the verification was successful; and
the fourth data of the prover device and the second data of the verifier device of a last verification operation being correct.
|