| CPC G06F 12/1408 (2013.01) [G06F 9/3877 (2013.01); G06F 9/45558 (2013.01); G06F 12/0802 (2013.01); G06F 21/57 (2013.01); G06F 21/602 (2013.01); G06F 21/606 (2013.01); G06F 21/64 (2013.01); G06F 21/76 (2013.01); G06F 21/79 (2013.01); H04L 9/0631 (2013.01); H04L 9/0637 (2013.01); H04L 9/083 (2013.01); H04L 9/0838 (2013.01); H04L 9/0844 (2013.01); H04L 9/085 (2013.01); H04L 9/0891 (2013.01); H04L 9/321 (2013.01); H04L 9/3215 (2013.01); H04L 9/3226 (2013.01); H04L 9/3268 (2013.01); H04L 9/3278 (2013.01); H04L 41/046 (2013.01); H04L 41/28 (2013.01); G06F 2009/45591 (2013.01); G06F 2009/45595 (2013.01)] | 14 Claims |
|
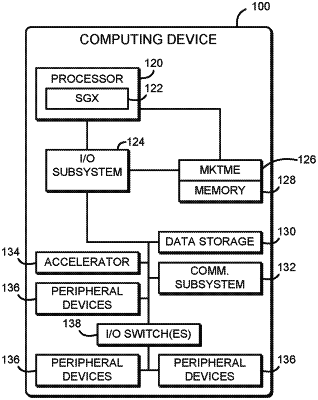
1. A computing device comprising:
processor circuitry coupled to a memory;
an input/output (I/O) device coupled to the processor circuitry; and
a trusted agent coupled to or hosted by the processor circuitry, the trusted agent to:
authenticate the I/O device;
perform an authenticated key exchange protocol with the I/O device in response to authentication of the I/O device;
verify a device configuration report in response to performance of the authenticated key exchange protocol, wherein the device configuration report is indicative of configuration registers of the I/O device; and
send the device configuration report to a trusted execution environment of the computing device in response to verification of the device configuration report, wherein the trusted execution environment includes a predetermined identify that is known to a trusted firmware component of the computing device.
|