| CPC H04M 3/568 (2013.01) [G06F 21/84 (2013.01); G10L 19/018 (2013.01); H04R 3/005 (2013.01)] | 14 Claims |
|
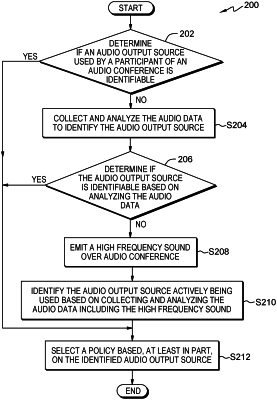
1. A computer-implemented method for detecting and concealing confidential communications, the computer-implemented method comprising:
responsive to a confidentiality mode being initiated for a audio conference, collecting audio data of an audio output source used by a participant of the audio conference;
generating an acoustic fingerprint from the audio data of the audio output source used by the participant;
comparing the acoustic fingerprint to known acoustic fingerprints of known audio output sources;
responsive to the acoustic fingerprint not matching the known acoustic fingerprints, emitting an inaudible sound signal to be played by the audio output source used by the participant;
responsive to detecting the inaudible sound signal via one or more microphones of one or more user devices used by one or more participants of the audio conference, determining that the participant is using an external speaker to listen to the audio conference; and
initiating a security measure to conceal confidential communications in the audio conference, the security measure including at least one of notifying the participant that the external speaker cannot be used to listen to the audio conference and blocking the external speaker.
|