| CPC H04L 9/0825 (2013.01) [H04L 9/0822 (2013.01); H04L 9/0894 (2013.01); H04L 9/14 (2013.01)] | 18 Claims |
|
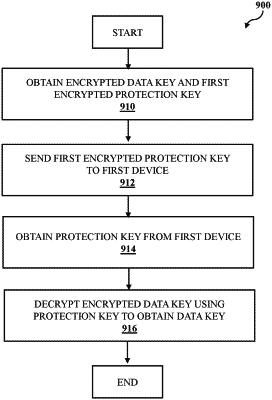
1. A computer-implemented method for data protection, comprising:
obtaining, by one or more processors, an encrypted data key and a first encrypted protection key from a storage device;
sending, by one or more processors, the first encrypted protection key to a first device;
receiving, by one or more processors, a second encrypted protection key from the first device, wherein the second encrypted protection key is generated by the first device through:
decrypting the first encrypted protection key, resulting in a protection key, and encrypting the protection key using a first session key;
decrypting, by one or more processors, the second encrypted protection key using a second session key; and
decrypting, by one or more processors, the encrypted data key using the protection key to obtain a data key.
|