| CPC H04L 63/1433 (2013.01) [H04L 63/1441 (2013.01); H04L 63/20 (2013.01); G06F 16/24578 (2019.01); G06F 16/285 (2019.01); H04L 41/12 (2013.01)] | 18 Claims |
|
1. A computer-implemented method, comprising:
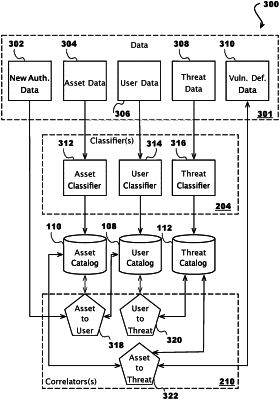
maintaining a plurality of data sets from a plurality of data sources, wherein individual ones of the data sets contain data about a plurality of assets, a plurality of users, or a plurality of threats associated with a network of computing assets;
augmenting the data in the data sets by classifying at least an asset in a first data set of the plurality of data sets, a user in a second data set of the plurality of data sets, and a threat in a third data set of the plurality of data sets;
receiving a query, wherein
the query is associated with a subject, and
the subject is an asset classification, a user classification, or a security threat classification;
selecting, based on the subject of the query, a machine learning correlator to infer a property of the network, wherein the machine learning correlator is selected from a set of correlators including (a) an asset-to-user correlator trained to identify correlations of data between one or more assets of the plurality of assets and one or more users of the plurality of users, (b) an asset-to-threat correlator trained to identify correlations of data between the one or more assets and one or more threats of the plurality of threats, and (c) user-to-threat correlator trained to identify correlations of data between the one or more users and the one or more threats;
generating a response to the query based on the property of the network inferred by the machine learning correlator selected; and
performing a security action affecting the subject, and the one or more assets, the one or more users, or the one or more threats, based on the inferring of the property of the network.
|