| CPC H04L 63/1425 (2013.01) [G06N 5/04 (2013.01); G06N 20/00 (2019.01); H04L 63/0876 (2013.01)] | 20 Claims |
|
1. A system, comprising:
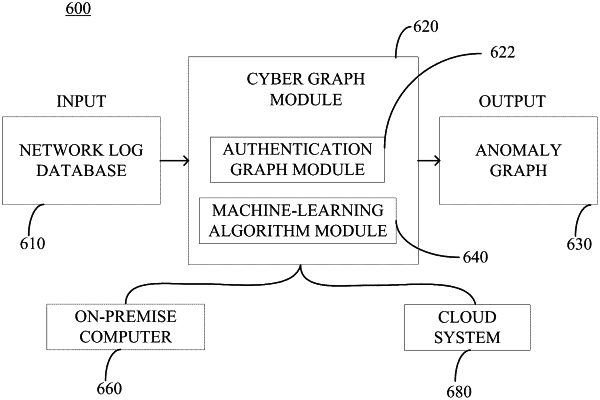
a log receiving module configured to receive a first plurality of network-level authentication logs having unique identifiers associated with users and services in a network, the network having a plurality of network entities each entity associated with a node, said first plurality of network-level authentication logs further having source Internet-Protocol addresses of a plurality of authentication entities from the plurality of network entities that request authentication, and a second plurality of network-level authentication logs having unique identifiers associated with a plurality of authentication events subject to an anomaly detection;
an authentication graph module configured to generate, according to the first plurality of network-level authentication logs, a network-level authentication graph of all the plurality of authenticating entities, wherein the authentication graph is a graph with a node type mapping and an edge type mapping for all of the nodes;
a sampling module configured to sample the authentication graph to generate a plurality of node sequences each including a sequence of nodes;
an embedding module configured to tune a plurality of node embeddings according to the plurality of node sequences, wherein each node embedding is a vector representation for a node;
a training module configured to train a link predictor according to the plurality of node embeddings and ground-truth edge information from the authentication graph;
a link prediction module configured to apply the link predictor to perform a link prediction on each of the plurality of authentication events subject to the anomaly detection; and
an anomaly detection module configured to perform anomaly detection of anomalous authentication between entities, wherein the anomaly detection detects lateral movement within the network of any of the plurality of authentication entities.
|