| CPC H04L 63/126 (2013.01) [H04L 67/562 (2022.05)] | 20 Claims |
|
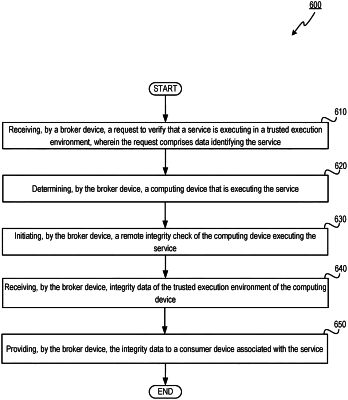
1. A method comprising:
receiving, by a broker device and from a first computing device, a request to verify that a service provided by a second computing device is executing in a trusted execution environment, wherein the request comprises data identifying the service;
initiating, by the broker device, a remote integrity check of the second computing device executing the service;
receiving, by the broker device, integrity data of the trusted execution environment of the second computing device;
verifying, by the broker device, the integrity data received from the second computing device by performing one or more operations to correlate the integrity data to the service provided by the second computing device;
generating combined integrity data by combining the integrity data received from the second computing device with integrity data associated with the broker device; and
providing, by the broker device, the combined integrity data to the first computing device associated with the service.
|