| CPC G06F 21/602 (2013.01) [G06F 16/2379 (2019.01); G06F 21/604 (2013.01); G06F 21/6209 (2013.01); G06Q 10/087 (2013.01); G06Q 10/0835 (2013.01); G06Q 20/389 (2013.01); G06Q 20/401 (2013.01); H04L 9/085 (2013.01); H04L 9/0827 (2013.01); H04L 9/0861 (2013.01); H04L 9/0877 (2013.01); H04L 63/0442 (2013.01); H04L 63/0823 (2013.01); H04L 63/0838 (2013.01)] | 19 Claims |
|
1. A system comprising:
a memory; and
a processor, operatively coupled to the memory, to perform operations comprising:
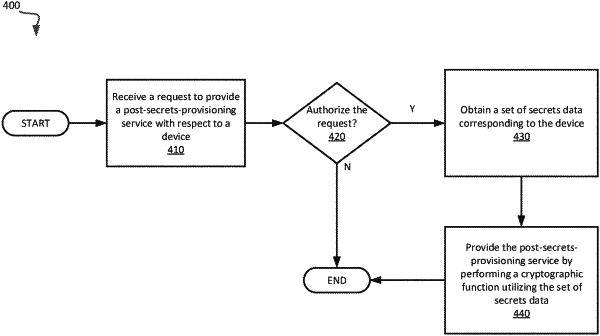
receiving a request to provide a post-secrets-provisioning service with respect to a device having a supply chain state corresponding to a supply chain associated with the device, wherein the supply chain state is one of: a manufacturing provisioning state corresponding to a manufacturing stage of the supply chain, a vendor provisioning state corresponding to a vendor stage of the supply chain, a network provisioning state corresponding to a network stage of the supply chain, or an operational state corresponding to an operational stage of the supply chain;
in response to receiving the request, determining whether to authorize the request based on a proof of ownership of the device;
in response to authorizing the request, obtaining a set of secrets data corresponding to the supply chain state of the device; and
emulating, by utilizing the set of secrets data, the device having the supply chain state to provide the post-secrets-provisioning service.
|