| CPC G06F 21/554 (2013.01) [G06F 2221/034 (2013.01)] | 15 Claims |
|
1. A guard system for preventing cyberintrusion of a protected processing environment, the guard system comprising at least one non-transitory computer-readable medium configured for storage of instructions executable by one or more security processors, the instructions which when executed by the one or more security processors cause the one or more security processors to:
when the guard system is in a training mode:
generate one or more test inputs associated with at least one data exchange between the protected processing environment and one or more external data sources via at least one interface;
observe, via one or more neural networks configured for execution on the one or more security processors, one or more training behavior sets of the at least one interface corresponding to the at least one data exchange, the one or more training behavior sets associated with at least one of 1) an assessment parameter of the data exchange or 2) an operational mode of the protected processing environment, the one or more training behavior sets including at least one optimal behavior set corresponding to a minimal threat of cyberintrusion;
generate, via the one or more neural networks, one or more system templates based on the one or more training behavior sets;
and
store the one or more system templates to memory accessible to the guard system;
and
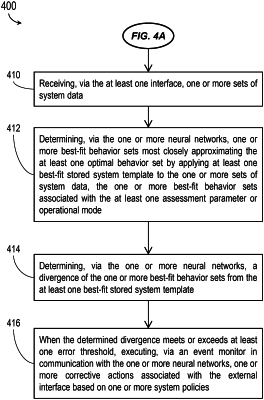
when the guard system is not in the training mode, for each exchange of system data between the one or more external data sources and the protected system via the at least one interface:
determine, via the one or more neural networks, one or more best-fit behavior sets most closely approximating the at least one optimal behavior sets by applying at least one best-fit stored system template to the received system data;
and
determine, via the one or more neural networks, a divergence of the one or more best-fit behavior sets from the at least one best-fit stored system template;
and
at least one event monitor configured for execution on the one or more security processors, operatively coupled to the at least one interface and including a policy database configured for storage of one or more system policies,
the event monitor configured to, if the determined divergence meets or exceeds a divergence threshold associated with the at least one interface, cause the one or more security processors to execute one or more corrective actions based on the one or more system policies associated with the at least one interface.
|