| CPC G06F 21/52 (2013.01) [G06F 2221/033 (2013.01)] | 26 Claims |
|
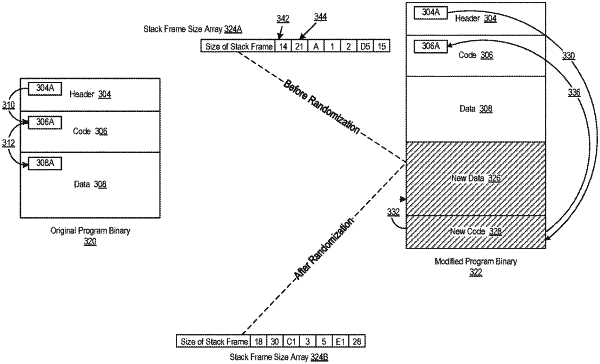
1. A method of defending against stack-based cybersecurity attacks that exploit vulnerabilities in buffer overflows of a stack register included as part of a random access memory (RAM) configured for storing local variables of a function included in a program binary comprising:
prior to loading of the program binary into the RAM and after compilation, transforming the program binary to include modifications that relate to stack frame size;
generating a random number offset;
determining a size of a stack space originally requested by the program binary;
generating a randomized stack size by adding the random number offset to the size of the stack space originally requested by the program binary;
replacing one or more instructions including the size of the stack space with the randomized stack size;
upon entry of program flow into the function, allocating stack space on the stack register in accordance with the randomized stack size; and
upon exit of program flow from the function, de-allocating the allocated stack space.
|