| CPC H04W 12/60 (2021.01) [H04L 63/102 (2013.01); H04W 12/037 (2021.01); H04W 12/041 (2021.01); H04W 76/18 (2018.02); H04W 76/19 (2018.02); H04W 76/27 (2018.02); H04W 80/08 (2013.01); H04W 92/10 (2013.01)] | 19 Claims |
|
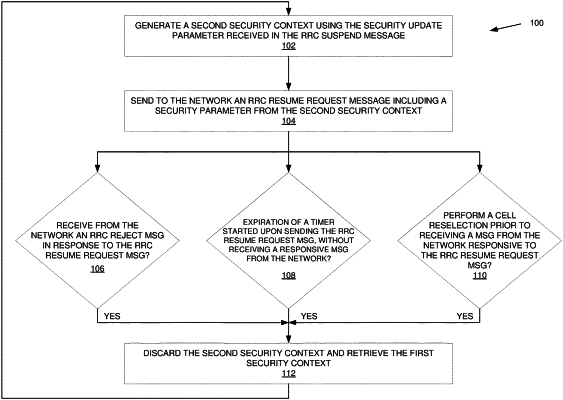
1. A method of updating a security context, performed by a wireless device operative in a wireless communication network employing a Radio Resource Control (RRC) protocol, wherein the wireless device in RRCCONNECTED state receives from the network an RRCSuspend message including a security update parameter, and in response to the RRC Suspend message enters an RRC INACTIVE state and stores a first security context, the method comprising, upon attempting to transition to an RRCCONNECTED state:
generating a second security context from the security update parameter received in the RRC Suspend message;
sending to the network an RRC Resume Request message;
receiving a response from the network to the RRC Resume Request message; and
performing an action based on the response wherein:
when the response is an RRC Reject message, the action is storing the second security context and utilizing the second security context until confirmed by the network; and
when the response is an RRC message different than the RRC Reject message, the action is discarding the first security context and using the second security context for further communication.
|