| CPC H04L 63/1441 (2013.01) [G06N 3/08 (2013.01); H04L 63/1416 (2013.01)] | 24 Claims |
|
1. A computer-implemented method for identifying and remediating zero-day attacks on a network, the method being executed by one or more processors and comprising:
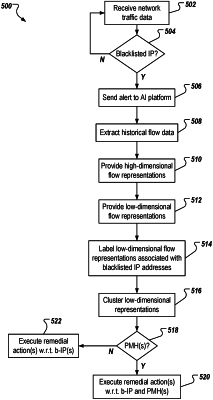
receiving flow data representative of communication traffic of the network;
determining that at least one blacklisted Internet protocol (IP) address is present in the flow data, the at least one blacklisted IP address representing a known malicious host, and in response:
retrieving historical flow data for the at least one blacklisted IP address, the historical flow data representing flow data associated with the at least one blacklisted IP address for a time period prior to determining that the at least one blacklisted IP address is present in the flow data,
providing a set of high-dimensional flow representations of network traffic by processing the historical flow data through a deep learning (DL) model, each high-dimensional flow representation in the set of high-dimensional flow representations comprising a high-dimensional vector representing a host within the historical flow data, the set of high-dimensional flow representations including all hosts represented within the historical flow data,
providing a set of low-dimensional flow representations of the network traffic from the set of high-dimensional flow representations by reducing dimensions of the high-dimensional flow representations in the set of high-dimensional flow representations, at least one low-dimensional flow representation representing the known malicious host within the network traffic and at least one low-dimensional flow representation representing an unknown malicious host within the network traffic, and
labeling at least a portion of the set of low-dimensional flow representations to provide a sub-set of labeled low-dimensional flow representations and a sub-set of unlabeled low-dimensional flow representations, each labeled low-dimensional flow representation representing a respective known malicious host; and
identifying a host associated with an unlabeled low-dimensional flow representation as a potentially malicious host by clustering the unlabeled low-dimensional flow representations in the sub-set of unlabeled low-dimensional flow representations in view of the labeled low-dimensional flow representations in the sub-set of the labeled low-dimensional flow representations, and in response, automatically executing a remedial action with respect to the potentially malicious host.
|