| CPC H04L 43/0894 (2013.01) [G06F 9/445 (2013.01); G06F 9/455 (2013.01); H04L 43/028 (2013.01); H04L 63/14 (2013.01); H04L 69/16 (2013.01); H04L 41/046 (2013.01); H04L 41/0806 (2013.01)] | 18 Claims |
|
1. A method, comprising:
performing, by one or more processors that implement a network sensor host in a network:
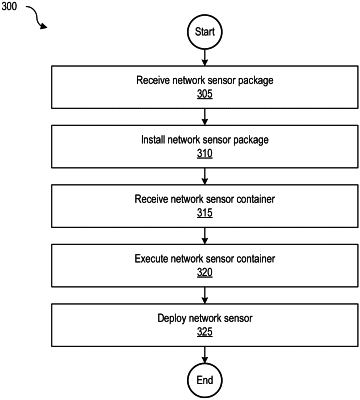
receiving a network sensor package from a network sensor deployment (NSD) server;
executing the network sensor package, wherein the execution comprises:
launching a container on network sensor host,
launching a network sensor inside the container, wherein the network sensor comprises:
(a) a deep packet inspection (DPI) application,
(b) an intrusion detection system (IDS) application, and
(c) an intrusion prevention system (IPS) application,
requesting configuration information for the network sensor from the NSD server, and
configuring the network sensor based on the configuration information, wherein the network sensor is configured to send status or health beacons to the NSD server, indicating one or more of: a link status of the network sensor, traffic rate(s) of the network sensor, drop rate(s) of the network sensor, memory usage of the network sensor, and a Switched Port Analyzer (SPAN) status of the network sensor;
collecting data about the network using the network sensor; and
sending the collected data to a remote cybersecurity platform monitoring the network.
|