| CPC G06Q 20/40 (2013.01) [G06Q 20/3226 (2013.01); G10L 25/51 (2013.01)] | 20 Claims |
|
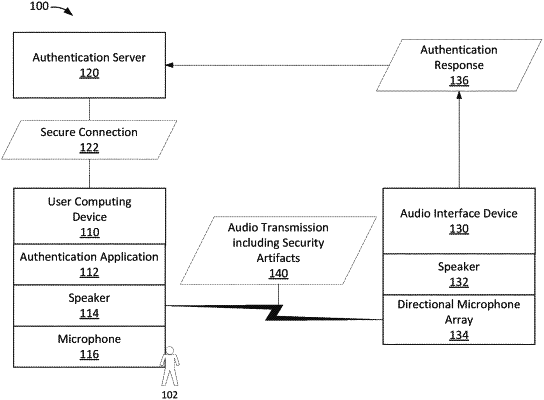
1. An authentication server computing device in network communication with an audio interface device and a verified user computing device, the authentication server computing device comprising at least one processor in communication with a memory, the processor programmed to:
receive a service request from the audio interface device, the service request including a service account identifier used by a suspect user to initiate the service request using the audio interface device;
generate a first audio file including a first audio transmission, the first audio transmission including a primary security artifact and at least one secondary security artifact, wherein the primary security artifact is an encoding of a one-time password;
store, in the memory, a reference data file including the first audio transmission;
transmit the first audio file including the first audio transmission to the verified user computing device, the verified user computing device associated in the memory with a legitimate user of the service account identifier;
receive a second audio file from the audio interface device in response to the verified user computing device automatically playing the first audio transmission for the audio interface device, the second audio file including a second audio transmission;
verify the second audio transmission by comparing the second audio transmission to the first audio transmission in the stored reference data file, including electronically comparing the second audio transmission to the first audio transmission to match the primary security artifact and the at least one secondary security artifact of the first and second audio transmissions;
verify the suspect user as the legitimate user of the service account identifier based on verifying the second audio transmission; and
authorize the service request based on the verification of the second audio transmission and the suspect user being the legitimate user.
|