| CPC G06F 8/65 (2013.01) [G01C 21/3453 (2013.01); G01C 21/3691 (2013.01); G05D 1/0212 (2013.01); G05D 1/0291 (2013.01); G06F 21/50 (2013.01); H04L 63/1433 (2013.01)] | 18 Claims |
|
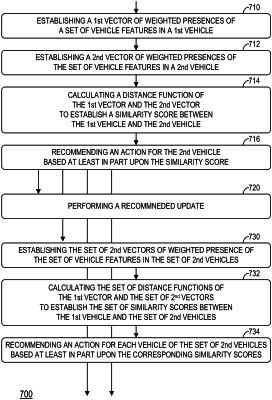
1. A method comprising:
establishing a first vector of weighted presences of a set of vehicle features in a first vehicle;
establishing a second vector of weighted presences of the set of vehicle features in a second vehicle;
calculating a distance function between the first vector and the second vector to establish a similarity score between the first vehicle and the second vehicle; and
recommending an action for the second vehicle based at least in part upon the similarity score,
wherein the set of vehicle features includes one or more attack paths that are present within a network topology of the first vehicle, the network topology of the first vehicle having a set of attack surfaces of the first vehicle and a set of Electronic Control Units (ECUs) of the first vehicle;
wherein the set of vehicle features includes one or more attack paths that are not present within a network topology of the second vehicle;
wherein each of the one or more attack paths of the network topology of the first vehicle is between an attack surface of the set of attack surfaces of the network topology of the first vehicle, and an endpoint at an ECU of the set of ECUs of the first vehicle;
wherein each of the one or more attack paths of the network topology of the first vehicle is weighted based upon an attack score; and
wherein the attack score of each of the one or more attack paths of the network topology of the first vehicle is based on at least one of: an inverse proportionality to a number of ECUs in the attack path; a number of hops between the attack surface of the attack path and the endpoint of the attack path; a severity of one or more vulnerabilities of or along the attack path; a difficulty of accessing the attack surface of the attack path; and a difficulty of overcoming or passing one or more ECUs in the attack path.
|