| CPC G06F 21/604 (2013.01) [G06F 21/64 (2013.01); H04L 9/0816 (2013.01); H04L 9/0894 (2013.01); H04L 9/3236 (2013.01); H04L 9/3271 (2013.01); G06F 21/602 (2013.01); G06F 2221/2149 (2013.01)] | 16 Claims |
|
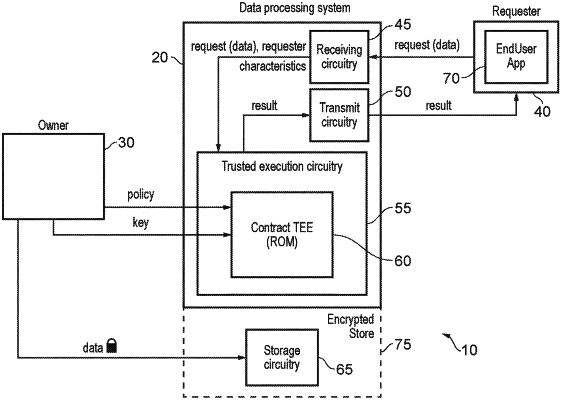
1. A data processing system comprising:
receiving circuitry configured to receive, from a requester, a request for the requester to use decrypted data obtained by decrypting encrypted data;
trusted execution circuitry configured to provide a trusted execution environment, wherein the trusted execution circuitry is configured to:
securely store a policy;
acquire a key within the trusted execution environment, wherein the key is associated with the decrypted or encrypted data; and
in response to the request and based on one or more characteristics of the requester and the policy, performing decryption on the encrypted data and transmitting the decrypted data to the requester.
|