| CPC G06F 21/56 (2013.01) [G06F 2221/034 (2013.01)] | 8 Claims |
|
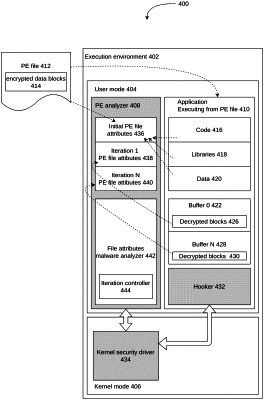
1. A computer-implemented method for training a machine-learning static analyzer based on iterative executable file analysis, the method executed on a processor, the method comprising the steps of:
a. retrieving file attributes from an untrusted file;
b. creating an attributes tree of the untrusted file's attributes;
c. performing iteration of dynamic analysis of the untrusted file including decryption of at least one encrypted data block of the untrusted file by intercepting an operation of decrypting the at least one encrypted data block during an execution of the untrusted file's code and updating the tree of the file attributes for the untrusted file based on the at least one decrypted data block;
d. repeating step (c) until the file's code has been executed;
e. training machine learning static analyzer based on the updated file attributes tree of the untrusted file and a classified files collection;
f. analyzing the untrusted the and a second untrusted file, wherein the second untrusted file was modified from the untrusted file after the execution; and
g. repeating the steps of intercepting and updating at least three times, wherein updating at least three times expands the file attributes tree with six additional attributes for analysis.
|