| CPC G06F 21/554 (2013.01) [G06F 2221/034 (2013.01)] | 20 Claims |
|
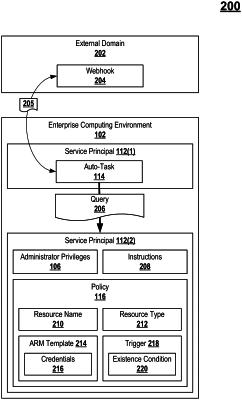
1. A computer-implemented method for identifying and mitigating an attack vector in a computing environment, comprising:
identifying a policy definition that is configured to cause generation of a virtual machine having access to a first permissions level that is lower than at least one second permissions level;
determining that a user account that is assigned the at least one second permissions level has been utilized to generate, at a first time, a first service principal and a second service principal that includes the policy definition and that is assigned the at least one second permissions level, wherein the second service principal is configured to update the virtual machine from having access to the first permissions level to having access to the at least one second permissions level;
identifying at least one trigger event associated with the first service principal that is configured to:
cause the second service principal to:
generate, at a second time, the virtual machine in accordance with the policy definition, and
update the virtual machine from having access to the first permissions level to having access to the at least one second permissions level by associating the virtual machine with a third service principal at the second time;
determining whether that the at least one trigger event is not restricted based on the at least one second permissions level; and
mitigating the attack vector by performing a predefined remedial action in response to determining that the at least one trigger event is not restricted based on the at least one second permissions level prior to an occurrence of the at least one trigger event.
|