| CPC G06F 21/552 (2013.01) [G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A method comprising:
maintaining, by a computer system running a security analytics program, information regarding historical process activity within a private network, wherein the private network includes a plurality of computing devices accessed by a plurality of users and wherein the information regarding historical process activity includes information regarding a plurality of processes hosted by the plurality of computing devices during one or more observation periods;
receiving, by the computer system, information regarding process activity within the private network for a current observation period;
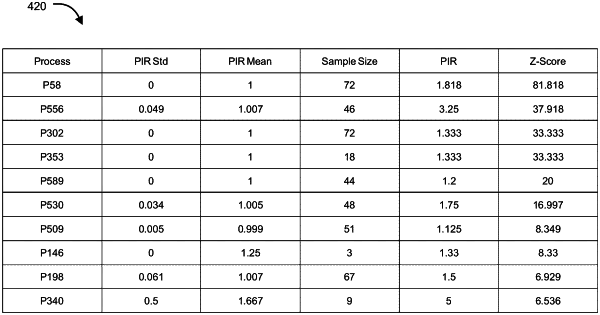
for each process of the plurality of processes, for each testing time period of a plurality of testing time periods within the current observation period, automatically determining without human interaction, by the security analytics program, a process interaction ratio (PIR) between (i) a number of unique computing devices of the plurality of computing devices, which host the process and (ii) a number of unique users of the plurality of users;
automatically identifying without human interaction, by the security analytics program, a particular process of the plurality of processes as being potentially malicious when a PIR z-score for the particular process during a testing time period of the plurality of testing time periods exceeds a pre-defined or configurable threshold, wherein the PR z-score is a measure of deviation of the PR of the particular process from a historical PR mean of the particular process; and
displaying to an administrator, by the security analytics program, to the particular process of the plurality of processes identified as being potentially malicious.
|