| CPC G06F 21/6254 (2013.01) [G06F 21/36 (2013.01); G16H 10/60 (2018.01); H04L 9/3213 (2013.01)] | 17 Claims |
|
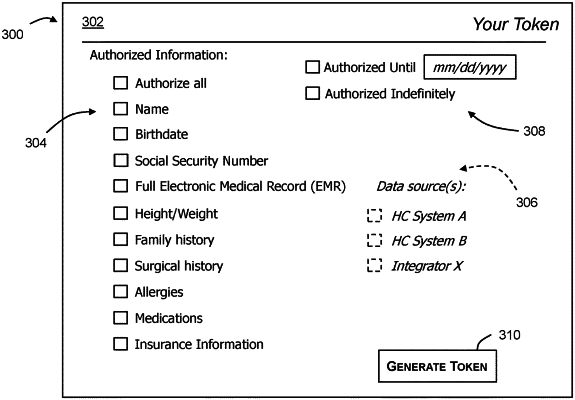
1. A data security system for enabling tokenized access to sensitive data, the data security system comprising a token provisioning computing device including a processor communicatively coupled to a memory device, the processor programmed to:
generate an access token that is associated with and enables access to defined sensitive data associated with a first data subject from one or more data sources according to one or more authorization parameters;
store the access token in a token database with the one or more authorization parameters, the one or more authorization parameters including a data source identifier indicating where the defined sensitive data is stored;
transmit the access token to a remote client computing device of the first data subject;
receive, from a service provider computing device separate from the remote client computing device, a data access request including an inputted access token;
compare the inputted access token to the access token stored in the token database;
when the inputted access token matches the stored access token, transmit, to the service provider computing device, the defined sensitive data being requested and associated with the stored access token;
receive, from the remote client computing device, data subject input indicating a revocation of the stored access token; and
using the data subject input, initiate at least one of delete the stored access token or disable the stored access token to prevent further access to the sensitive data by the service provider computing device.
|