| CPC H04L 63/145 (2013.01) [H04L 63/0209 (2013.01); H04L 63/0263 (2013.01); H04L 63/1425 (2013.01)] | 31 Claims |
|
31. A computer software product for protecting a computing system against malicious command and control (C&C) channels to fixed Internet Protocol (IP) addresses, the product comprising a non-transitory computer-readable medium storing program instructions, when read by a computer, cause the computer:
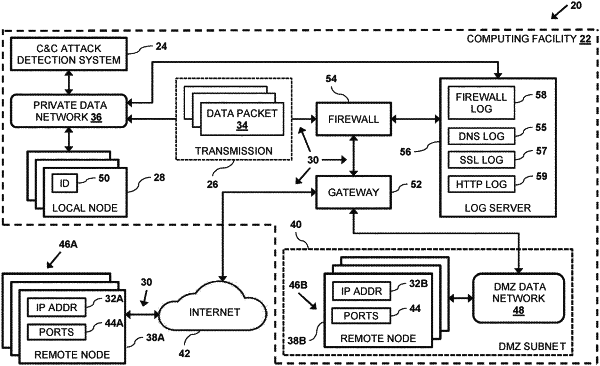
to collect information extracted from data traffic transmitted between multiple local nodes on a private data network and public Internet Protocol (IP) addresses corresponding to multiple remote nodes on a public data network;
to detect, in the collected information, Domain Name System (DNS) resolutions requested by local nodes, each DNS resolution identifying a local node requesting a resolution with respect to a uniform resource identifier (URI) and a publicIP address corresponding to the URI received by the local node in response to the requesting the resolution;
to create a dataset comprising first publicIP addresses that were resolved by the DNS resolutions and received by the local nodes in the DNS resolutions detected in the information extracted from the data traffic,
to detect, in the collected information, transmissions from the local nodes that are addressed to second public IP addresses at respective times,
to compare the second publicIP addresses to the dataset comprising the first publicIP addresses to identify any of the detected transmissions that are addressed to any of the second publicIP addresses as the fixed IP addresses that are not included in the dataset comprising the first public IP addresses that were resolved previously by the DNS resolutions as suspicious transmissions, and
to initiate a protective action with respect to at least some of the identified suspicious transmissions.
|