| CPC H04L 63/1425 (2013.01) [H04L 63/0218 (2013.01); H04L 63/0254 (2013.01); H04L 63/145 (2013.01)] | 13 Claims |
|
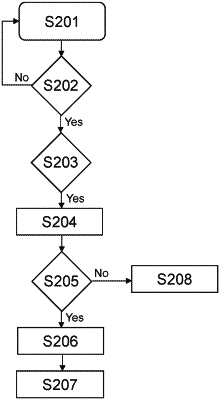
1. A method of threat detection, the method comprising:
detecting a new process that starts at a network node of a computer network;
determining that said new process requires external code modules by processing file contents of an executable image associated with said new process to retrieve a list of expected external code modules for the new process, wherein the list includes all external code modules that are used by the new process;
observing the times at which one or more of the external code modules in the list of expected external code modules for the new process are loaded relative to a start of the new process;
determining whether one or more external code modules that are not in the list of expected code modules for the new process are loaded;
determining that usage of an external code module is anomalous when the time elapsed between the start of the new process and loading of said external code module lies outside predetermined expected boundaries or said external code module was determined to be not in the list of expected code modules for the new process; and
taking further action to protect the network node and/or the computer network based on the determining that the usage of the external code module is anomalous.
|