| CPC H04L 63/1416 (2013.01) [G06F 16/907 (2019.01); G06F 21/55 (2013.01); H04L 63/1433 (2013.01)] | 20 Claims |
|
1. A computer-implemented method, comprising:
under control of one or more processors:
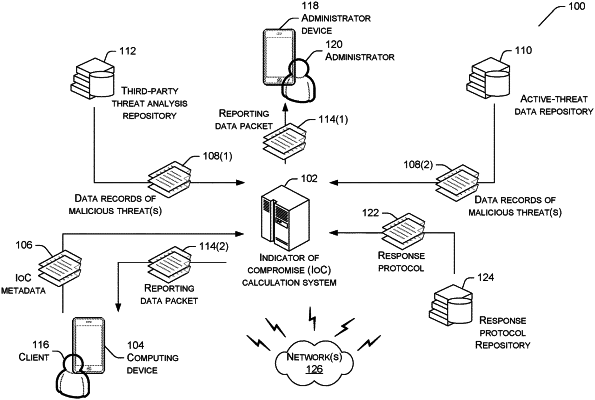
receiving, from a computing device operating on a telecommunications network, Indicator of Compromise (IoC) metadata derived from a client interaction at the computing device via the telecommunications network, the client interaction involving at least one of a change to a systems configuration file or a bypass of a communications channel;
analyzing the IoC metadata to identify data patterns between the IoC metadata and one or more malicious threats;
identifying at least one malicious threat from the one or more malicious threats, based at least in part on analysis of the IoC metadata;
retrieving, from a third-party data repository, a data record associated with the at least one malicious threat, the data record including a point-in-time that the at least one malicious threat was reported active;
performing a mitigation analysis of environmental criteria of the computing device that mitigate an effect of the at least one malicious threat on the computing device using the data record;
determining a vulnerability score that is associated with the at least one malicious threat, wherein the vulnerability score is determined to numerically combine a severity of the at least one malicious threat and mitigating environmental criteria;
determining a time-period for which the at least one malicious threat is to remain active after the point-in-time, wherein the time-period remains undefined for the at least one malicious threat that is difficult to mitigate, quarantine, or protect against; and
generating reporting data that includes at least the vulnerability score associated with the IoC metadata.
|